Security alarms are used in residential commercial industrial and military properties for protection against burglary or property damage as well as personal protection against intruders security alarms in residential areas show a correlation with.
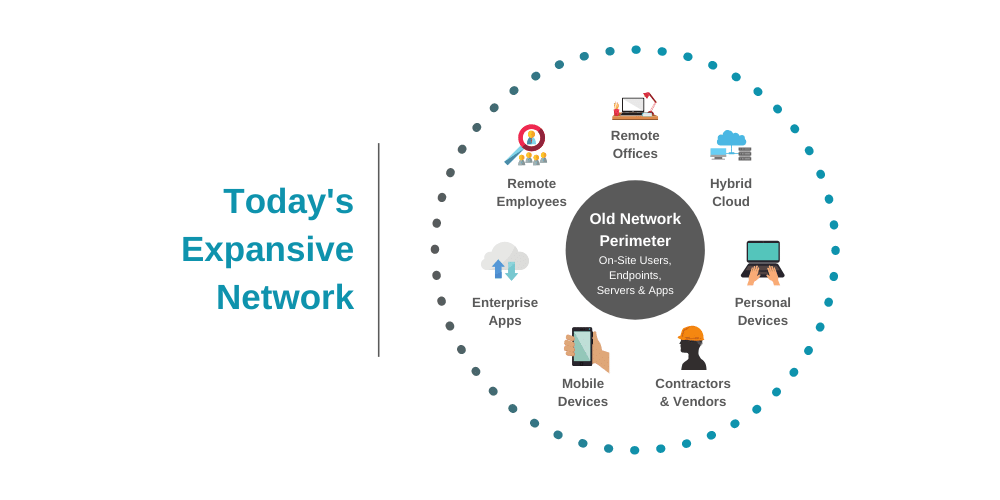
Perimeter access control is the iot applications related to which area.
Iot devices connecting to iot platforms.
Iot applications promise to bring immense value into our lives.
Protocols are used based on the application area and not all protocols are.
Access control is about controlling access whereas perimeter security is actually used to prevent access and of course deter detect and delay intruders in many instances he noted access control and alarms complement each other as perimeter security generally include gates barriers and other access points that need to be controlled.
More than 50 billion devices will be connected to the internet by 2020 but this new connectivity revolution has already started.
Access control includes the control of persons vehicles and materials through entrances and exists in a controlled area or premises.
Iot applications are expected to equip billions of everyday objects with connectivity and intelligence.
Find and compare leading iot companies.
There is a more recent 2018 ranking of top iot applications which can be found here.
Perimeter security and access control systems protect the external perimeters of a facility control access to restricted areas and detect and monitor anomalies.
The primary issue the iot facing is unauthorized access to rfid.
With newer wireless networks superior sensors and revolutionary computing capabilities the internet of things could be the next frontier in the race for its share of the wallet.
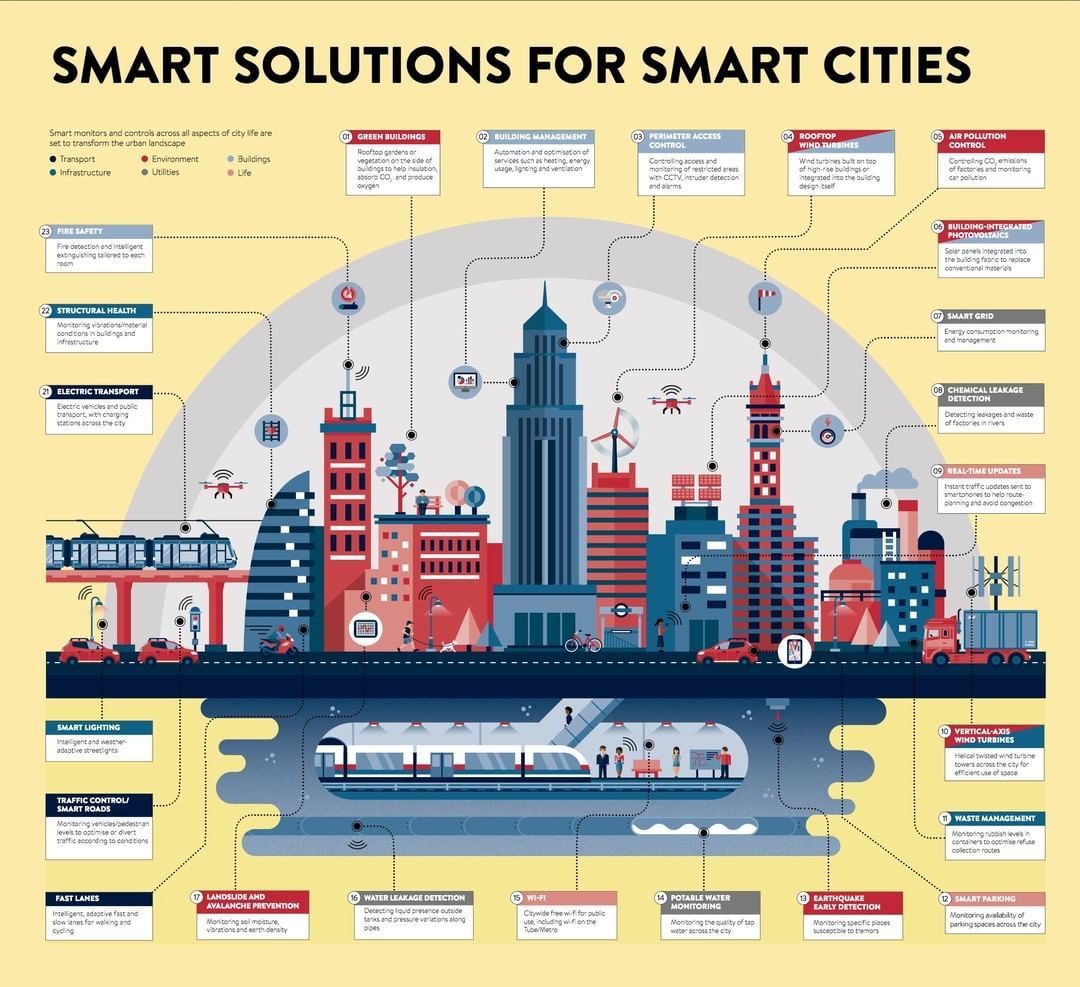
Iot solutions in the area of smart city solve traffic congestion problems reduce noise and pollution and help make cities safer.
Perimeter access control detects and controls.
Libelium publishes a compilation of 50 cutting edge internet of things applications grouped by vertical markets.
A security alarm is a system designed to detect intrusion unauthorized entry into a building or other area such as a home or school.
With access to all of iot analytics paid content and reports including dedicated analyst time.
Unlike cyber hacks where access and information are compromised in the digital domain the iot security threats have more far reaching and irreversible physical consequences.